This is an old revision of the document!
Okta
- Login to your okta account and navigate to the admin pages.
- Add an application by clicking "Applications" in the main menu. Click the "Add Application" button in the top, then press the "Create New App" button. Select "Web" as the platform and "OpenID Connect" as the Sign on method.
- Give you application a name and enter "https://[BLOCKS-IP]/rest/auth/callback?client=OidcClient" as the "Login redirect URI".
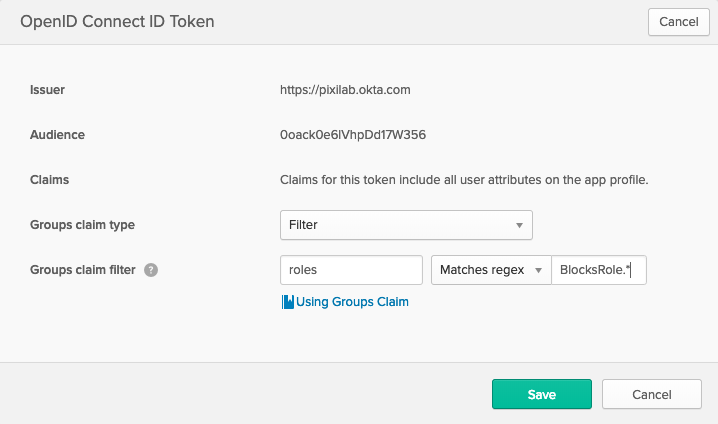
- Select the "Sign On" tab at the top of your application page. Scroll down and press the "Edit" button at the top of the "OpenID Connect ID Token" section. Adjust the values to match the ones on the image below.
- Click on the "Directory" button in the main menu and select "Groups".
- Click the "Add Group" button and give it the name of "BlocksRoleAdmin". Repeat the process until you end up with the following roles listed:
- BlocksRoleAdmin
- BlocksRoleManager
- BlocksRoleCreator
- BlocksRoleEditor
- BlocksRoleContributor
- BlocksRoleStaff
- Click on the "BlocksRoleAdmin" role to edit the role.
- At the top, click the "Manage Apps" button and assign in to your application. Close the window and click the "Manage People" button (next to "Manage Apps"). Assign members to the group and click "Save". Repeat this process with all of the groups, assign them to your application and add members that you want to represent each group.
- Click on the "Applications" button in the main menu and select your newly created application. Click on the General tab and locate the "Client Credentials" section at the bottom. Note the values for "Client ID" and "Client secret" for use in step 10.
- Open your server configuration file and add the "auth" section below to the allready existing "server" section. Replace the values of [BLOCKS-IP], [YOUR-OKTA-SUBDOMAIN], [CLIENT-ID] and [CLIENT-SECRET]. [YOUR-OKTA-SUBDOMAIN] is visible as "Issuer" in the "OpenID Connect ID Token" section of the "Sign On" tab (see step 4).
server:
auth:
urlResolver: null
ajaxRequestResolver: null
callbackUrl: https://[BLOCKS-IP]/rest/auth/callback
rolesOwner: attributes
rolesPath: roles
rolesMapping:
BlocksRoleAdmin: Admin
BlocksRoleManager: Manager
BlocksRoleCreator: Creator
BlocksRoleEditor: Editor
BlocksRoleContributor: Contributor
BlocksRoleStaff: Staff
clients:
- org.pac4j.oidc.client.OidcClient:
configuration:
discoveryURI: [YOUR-OKTA-SUBDOMAIN]/.well-known/openid-configuration
clientId: [CLIENT-ID]
secret: [CLIENT-SECRET]
clientAuthenticationMethod: client_secret_basic
scope: openid profile groups
servlet:
security:
- matchers: internalMatcher
clients: OidcClient
authorizers: isAuthenticated
Start Blocks and go to "/edit" for login.