Table of Contents
Blocks single-sign-on using OKTA
This article describes how to set up Blocks single-sign-on using the popular OKTA SSO service provider.
- Login to your okta account and navigate to the admin pages.
- Add an application by clicking "Applications" in the main menu. From the options that show up, proceed to select "Applications". Click the "Create App Integration" button at the top. Select "OIDC - OpenID Connect" as the Sign-in method and "Web Application" as the Application type. Click "Next".
- Give you application a name and enter "https://[BLOCKS-IP]/rest/auth/callback?client_name=OidcClient" as the "Sign-in redirect URIs". Scroll down, and under "Assignments", select the option that suits you better. Click the "Save" button to finish this creation.
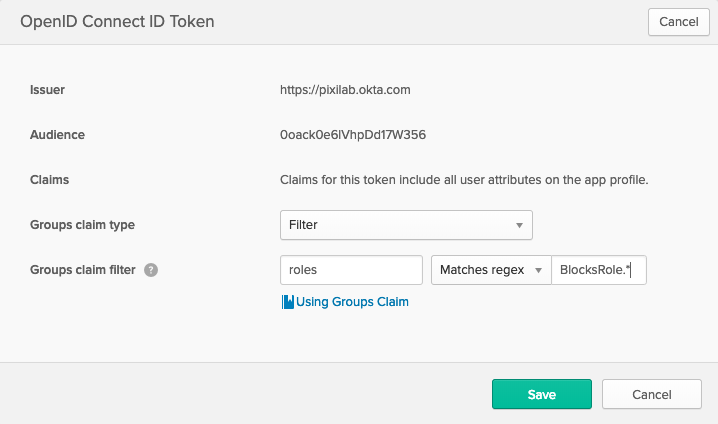
- Select the "Sign On" tab at the top of your application page. Scroll down and press the "Edit" button at the top of the "OpenID Connect ID Token" section. Adjust the values to match the ones on the image below. What this means is that when Okta sends information about a specific user back to Blocks, after a successful authentication, it will include all of the user's groups – renamed to roles – in the user data. Note that the "BlocksRole.*" only include the roles that starts with "BlocksRole". If you name your roles differently you'd have to adjust this value.
- Click on the "Directory" button in the main menu and select "Groups".
- Click the "Add Group" button and give it the name of "BlocksRoleAdmin". Repeat the process until you end up with the following roles listed:
- BlocksRoleAdmin
- BlocksRoleManager
- BlocksRoleCreator
- BlocksRoleEditor
- BlocksRoleContributor
- BlocksRoleStaff
- Click on the "BlocksRoleAdmin" role to edit the role.
- At the top, click the "Applications" button and assign it to your application. Close the window and click the "People" button (next to "Applications"). Assign members to the group and click "Save". Repeat this process with all of the groups, assign them to your application and add members that you want to represent each group.
- Click on the "Applications" button in the main menu and select your newly created application. Click on the General tab and locate the "Client Credentials" section. Note the values for "Client ID" and "Client secret" for use in step 1 of the Blocks specific section below.
Blocks specific steps
- Open your Blocks configuration file on your Blocks server and add the "auth" section below to the already existing "server" section. Replace the values of [BLOCKS-DOMAIN-OR-IP], [YOUR-OKTA-SUBDOMAIN], [CLIENT-ID] and [CLIENT-SECRET]. [YOUR-OKTA-SUBDOMAIN] is visible as "Issuer" in the "OpenID Connect ID Token" section of the "Sign On" tab (see step 4).
server: type: pixilab_server auth: urlResolver: null ajaxRequestResolver: null callbackUrl: http://[BLOCKS-DOMAIN-OR-IP]/rest/auth/callback rolesOwner: attributes rolesPath: roles rolesMapping: BlocksRoleAdmin: Admin BlocksRoleManager: Manager BlocksRoleCreator: Creator BlocksRoleEditor: Editor BlocksRoleContributor: Contributor BlocksRoleStaff: Staff clients: - org.pac4j.oidc.client.OidcClient: configuration: discoveryURI: [YOUR-OKTA-SUBDOMAIN]/.well-known/openid-configuration clientId: [CLIENT-ID] secret: [CLIENT-SECRET] clientAuthenticationMethod: client_secret_basic scope: openid profile groups servlet: security: - matchers: internalMatcher clients: OidcClient authorizers: isAuthenticated applicationConnectors: useForwardedHeaders: true
- Start Blocks and go to "/edit" for login.
Role Mapping
When the roles (through groups) you've added to your Okta configuration does not match the roles used by blocks, as per our description in the section above (step 6). You can add role mapping to the Blocks configuration file. You do this by defining a server.auth.rolesMapping parameter where the keys are the roles of your Okta configuration and the values the roles Blocks know about. For example:
rolesMapping: BlocksRoleAdmin: Admin BlocksRoleManager: Manager BlocksRoleCreator: Creator BlocksRoleEditor: Editor BlocksRoleContributor: Contributor BlocksRoleStaff: Staff
This mapping is already included in the configuration example, but it can be a good thing to keep in mind if your roles look different from what we configured in step 6 of the section above.